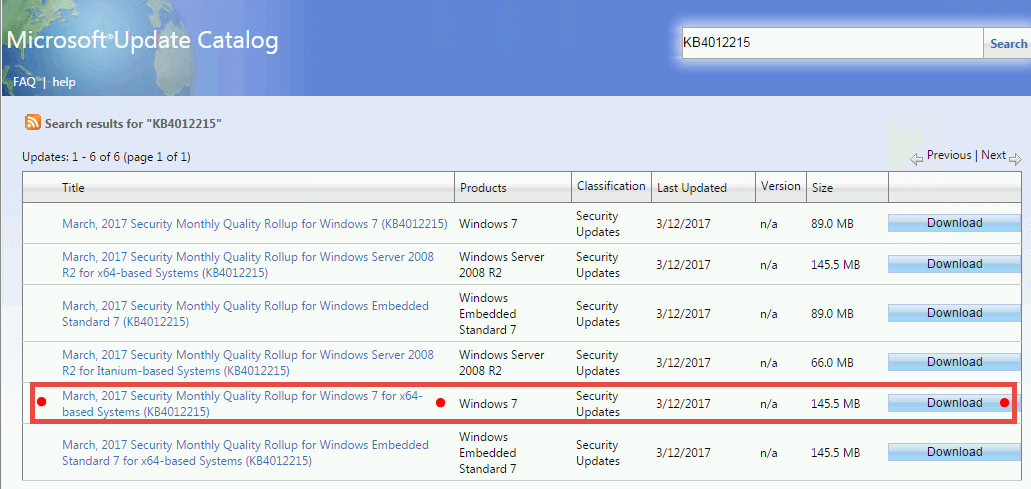
May 04, 2018 Windows 7 Pro Patch for WannaCry I'm trying to determine if Windows 7 Pro was patched to protect it from WannaCry. If there was a patch, I'm also trying to determine how to verify that I received the update including the patch.
Windows 7 Patch Download
Is there any security patch (Vulnerability of MS17-010) available for Windows 2000 Server? Jun 15, 2017 Watch video Windows WARNING: This is probably the most important update you will EVER need to install. To download from Microsoft’s Download Centre or Windows Update. Hit by the WannaCry malware were.
WannaCrypt also termed as WannaCry and Wcry or Wcrypt, has already caused massive damage worldwide through its NSA-powered ransomware. The ransomware has reportedly attacked businesses, hospitals, railways stations, universities and many other organizations inflicting a major devastation.
WannaCrypt ransomware targets outdated systems
A common observation among the targeted systems is that many of them were running older Windows operating systems like Windows XP, Windows 8 and Windows Server 2003. Such systems usually do not get Microsoft support unless the organization using them opt for special custom support.
Microsoft releases Patches for Windows XP, etc
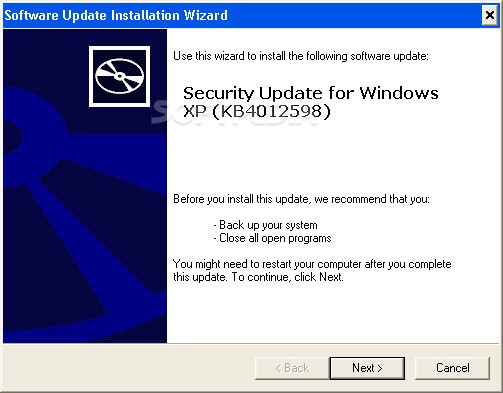
To counter this emergency situation and spread of the malware, Microsoft has released emergency fixes in the form of security patches to defend against the malware. The company even released WannaCrypt Patches for the unsupported versions of Windows OS, such as Windows XP, Windows 8 and Windows Server 2003, as well as for the supported platforms.
Describing this emergency step as highly unusual one, Microsoft said that it is providing a security update for all customers to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003.
Customers running Windows 10 were not targeted by the attack, said the company.
Patch your Windows OS right now!
For those who are still running older Windows versions, it’s time that you should patch immediately. Moving to the latest Windows version is also a good idea as Microsoft says that Windows 10 isn’t targeted.
Users who have enabled Windows Update are already protected as they will receive patch automatically. For customers using Windows Defender, Microsoft has already released an update which detects the threat as Ransom:Win32/WannaCrypt. As an additional “defense-in-depth” measure, keep up-to-date anti-malware software installed on your machines. Customers running anti-malware software from any number of security companies can confirm with their provider, that they are protected.
In case you are not able to install the patch on your PC, try following options,
- Disable SMBv1 with the steps documented at Microsoft Knowledge Base Article 2696547
- Add a rule on your router or firewall to block incoming SMB traffic on port 445
If you are lucky to haven’t been infected, make sure your security patches are up to date. Start by killing off the SMBv1, and block access to it from outside your network. As you know that there are patches already available for the malware codes, so there’s no excuse for getting caught out as a private user.
Remember to initiate the security steps urgently, as WannaCry ransomware demands $300 Bitcoin for unlocking encrypted files and the amount doubles after three days. Once infected, you are likely to receive threats that your files may be deleted permanently if the ransom is not paid within a week.
To get the download links and more information, visit this Technet post. Security patches are available for Windows Server 2003 SP2 x64, Windows Server 2003 SP2 x86, Windows XP SP2 x64, Windows XP SP3 x86, Windows XP Embedded SP3 x86, Windows 8 x86, Windows 8 x64.
Related Posts:
Following the massive Wana Decrypt0r ransomware outbreak from yesterday afternoon, Microsoft has released an out-of-bound patch for older operating systems to protect them against Wana Decrypt0r's self-spreading mechanism.
The operating systems are Windows XP, Windows 8, and Windows Server 2003. These are old operating systems that Microsoft stopped supporting years before and did not receive a fix for the SMBv1 exploit that the Wana Decrypt0r ransomware used yesterday as a self-spreading mechanism.
That mechanism is a modified version of the ETERNALBLUE exploit, an alleged NSA hacking tool leaked last month by a group known as The Shadow Brokers.
Original MS17-010 patch didn't include XP/Win8 fixes
Microsoft had released a fix for that exploit a month before, in March, in security bulletin MS17-010. That security bulletin only included fixes for Windows Vista, Windows 7, Windows 8.1, Windows 10, Windows Server 2008, Windows Server 2012, and Windows Server 2016.
As the SMBv1 is a protocol that comes built-in with all Windows versions, the computers which did not receive MS17-010 remained vulnerable to exploitation via Wana Decrypt0r's self-spreading package.
'Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download,' Microsoft said in a statement. 'This decision was made based on an assessment of this situation, with the principle of protecting our customer ecosystem overall, firmly in mind.'
Researchers believe that Wana Decrypt0r — also referenced online as WCry, WannaCry, WannaCrypt, and WanaCrypt0r — infected over 141,000 computers.
While unconfirmed, many believe older Windows XP and Windows Server versions were the bulk of the infections pool, as they had no way to protect themselves.
Patch systems and disable SMBv1 where possible
Download Wannacry Patch For Windows 7
Besides installing these out-of-band updates — available for download from here — Microsoft also advises companies and users to disable the SMBv1 protocol, as it's an old and outdated protocol, already superseded by newer versions, such as SMBv2 and SMBv3.
The current Wana Decrypt0r outbreak has been stopped last night after a security researcher found a kill switch. This is only temporary, as the attackers could release a new version of this threat. This is why patching the SMBv1 exploit is a better solution.
For those affected, you can discuss this ransomware and receive support in the dedicated WanaCrypt0r & Wana Decrypt0r Help & Support Topic. Bleeping Computer also published a technical analysis of the Wana Decrypt0r ransomware.